MCC2024 - Step Up

MCC (Malaysia Cybersecurity Camp) 2024 with the theme of “Step Up” was a four days cybersecurity camp that held at Pacific Regency Beach Resort in Port Dickson. The camp starts from 29th November to 2nd December. It brought together passionate students, cybersecurity practitioners and tinkers for a full intensive and practical sessions facilitated by industry professionals, guest speakers and skilled trainers. In keeping with the theme of “Step Up”, the camp’s main focus is to level up through lab sessions, web-app vulnerability research, RE exercises and alot of yapping and banter sessions, which gave alot insightful industry experiences and not just knowledge, also the wisdom.
0x00 Recon & Entrypoint
The init phase, it all started by registering my interested for MCC2024 at MCC website. After a few months, I made it onto the shortlist and was giving a next challenge which is to solve CTF challenges and submit a writeup. The last stage was an interview session with MCC agents, a quick but focused conversation about my background and what made me to be interested to join MCC. A month later, I received this email:
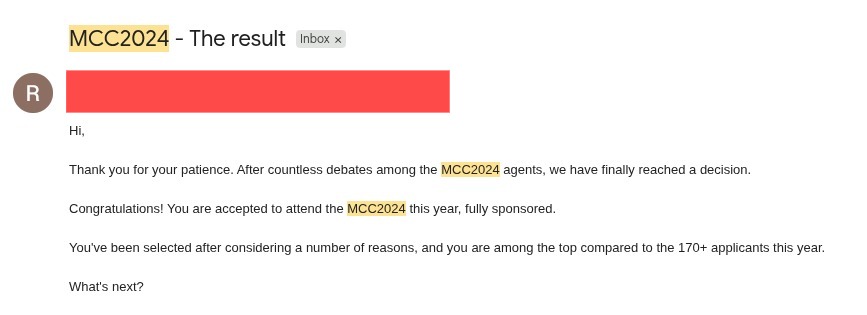
Wooo Hoooo LETS GOO MCC2024 !!!
0x01 Booting Up:Day1

So the day 1, beginning with a guest speaker Ain gave a talk about her career journey in cybersecurity. She shares her early struggles and motivation that made her never stops evolving. It sets the tone for the camp where we are still young and have the time and effort to adapt, learn and keep striving hard in our future cybersecurity careers. After that, we continue with CompTIA sharing session, which packed with insights on certifications, how it able to assist in career progression in order to stay relevant in the cybersecurity field. The day shifted gears with team-based incebreaks to get everyone talking in morse code…jk…we speak like normal human. Finally at night which is Lockpicking Night where we got ours hands dirty (for my case sweaty) with breaking locks.


0x02 OPS RE:Day2

For day 2, I chose the Reverse Engineering session which led by Azlan. The session began with learning how to create a crackme using C in Windows. After that, we disassembled the binary using IDA, demostrating how to read assembly and using x32dbg to debug it. It was a solid blend of theory and practice, and the kind of workshop where you leave with both new tools and new mental models for approaching binaries. For the materials used during RE session is available at Github and I also manage to create some crackme during the session, also at Github.

After RE session, we got a pair of sponsor sessions that added serious cred to our learning process. Nexagate walked us through how operate and serviing 400+ clients in Southeast Asia region providing SOC operation. Meanwhile, Velum Labs also share some insights of unseen attack vectors, simulate adversaries which help clients to anticipate threats.

During the night, we were given a boot2root challenge in which we need to work as a team and get the flag. Learn a lot about port knocking and CUPS vulnerability, and my teammates are: Harraz, Syamil, Lee Jia Poh and Naomi. Feel free to read the writeup at here
0x03 Web Exploits:Day3

Next day, we started off with Web Application Vulnerability Research by Ramadhan. We learn about PHP and Laravel, Rempah walk us through logic flows and misconfigurations in web applications. After that, guests that afternoon included representatives from Akati Sekurity, led by experienced folks behind one of Malaysia’s foremost cybersecurity firms. Founded in 2007, the company delivers managed security services, consulting, incident response, and governance across five continents. They bring strategy, intelligence, and resilience. Next was Google Cloud Security session which convered cloud incident handling and how VirusTotal is utilize as a tool for their threat intelligence operation.
The evening cooled down with a BBQ dinner and some social engineering…i mean social activity, conversing and sharing stories.


0x04 Exfiltration & Impact Phase:Day4

Now the final day, took group photos and in terms of MITRE ATT&CK terms, this was the exfiltration and packing up valuable intel we gathered through the course of 4 days. What we gathered ? skills, knowledge, wisdows, connections, friendship. By noon, MCC2024 network went offline as everyone checked out and headed their separate ways.
Post-Op Debrief
Looking back, MCC2024 was more than just a 4 day cybersecurity camp. It was a learning environment to stress-test my skills and being adaptive to learn more. Surrounding myself with positive minded and passionate people was the most valuable part, as they help nurture growth and push you to improve. Beyond the technical gains, the camp reinforced the value of community by having people to constantly share tools, ideas and new knowledge which indeed make the learning curve less steep and the journey more engaging. Now what is left for me is to share back the knowledge I learn back to the community and keep learning and progressing. Finally, a big thank you to RE:HACK, Mr Yap, and the MCC agents for all their effort in making this possible. Also not to forget, sponsors and support from various organization and individuals who contribute for making MCC2024 a huge success, their efforts have left a lasting impact on us.

- That’s me hacking on a ironboard, tee-hee :)